
Complete Data Security Guide: Protecting Your Business and Customer Information
Ship fast, safely - The minimum set of security practices that meaningfully drop your risk without slowing delivery

Table of Contents
- "Ship fast, safely"
- 1. Start with security during design
- 2. Control access with least privilege
- 3. Authentication that resists real attacks
- 4. Encryption that actually protects users
- 5. Network security: segment and observe
- 6. Secure development by default
- 7. Manage third parties with evidence, not promises
- 8. Keep security current
- 9. Physical security still matters
- 10. What to diagram
- Appendix: "Secure by default" settings you can adopt this week
- Notes on fact-checking and standards used
"Ship fast, safely"
Most breaches are not zero-days. They are missed basics: over-collected data, flat networks, weak auth, silent logs. The fastest teams ship features and security together by choosing a few non-negotiables and automating them in CI/CD.
This guide shows the minimum set that meaningfully drops your risk without slowing delivery. It is based on lessons regulators publish after real incidents and on open standards developers already use.
Data Lifecycle Security Controls
1. Start with security during design
Treat security like performance budgets: decide up front what you will and will not do. The FTC's first lesson from enforcement actions is simple: do not collect data you do not need. You cannot lose what you do not have. Build "why do we need this field?" into PR reviews and form schemas.
Developer checklist
- Remove nonessential fields from forms and APIs.
- Add unit tests that fail if new PII fields appear without a "purpose" annotation.
- Set default retention to the shortest viable period.
- For payments, never store Sensitive Authentication Data after authorization, and minimize any PAN retention. Tokenize when possible.
- Use synthetic data in dev and training. Never mirror production PII into lower environments.
Prompts to tailor this to your product
- Which tables or event streams contain PII you never query?
- Where could a token replace raw identifiers?
2. Control access with least privilege
Grant access only on a need-to-know basis. Apply least privilege for users, services, and pipelines. Restrict admin rights to the smallest set and time-box elevation. These are table-stakes in NIST 800-53 (AC-6) and CIS Controls.
Developer checklist
- Map roles → permissions. Enforce via IAM policies or RBAC/ABAC, not ad-hoc allow-lists. Review quarterly.
- Require just-in-time admin with MFA for break-glass flows. Log every elevation.
- Separate production data access from routine engineering work. Use read-only bastions and audited queries for support.
Prompts
- Who can reset user passwords today?
- Which services still run with wide "*" permissions?
3. Authentication that resists real attacks
Modern guidance shifted from brittle complexity rules to length, screening, and throttling. NIST 800-63B recommends allowing long passphrases, checking new passwords against breach corpuses, and applying rate-limiting to stop guessing and stuffing. Many orgs set 12+ characters as a practical floor while accepting even longer phrases.
Developer checklist
- Enforce long passwords or passphrases and screen against known-compromised lists.
- Add step-up MFA for sensitive actions.
- Implement per-account and global rate limits or progressive delays on failed login.
- Hash with a slow, memory-hard algorithm (Argon2id preferred; bcrypt/scrypt acceptable).
Prompts
- Do we screen new passwords against a breached list?
- Where do we still skip MFA because "it was hard to wire in"?
4. Encryption that actually protects users
Use standard, reviewed crypto and configure it correctly. NIST SP 800-52r2 and the UK NCSC advise TLS 1.2 configured with approved cipher suites and support for TLS 1.3. Do not disable certificate validation in apps. That makes HTTPS behave like HTTP and enables man-in-the-middle attacks, a failure class documented in OWASP's mobile guides.
Developer checklist
- Force TLS 1.2+ on every inbound and outbound hop. Prefer TLS 1.3. Pin where appropriate.
- Keep data encrypted in transit and at rest. Manage keys outside app repos and rotate on a schedule.
- Mobile: never override TrustManager or WebView SSL errors in production. Add tests that fail builds if cert validation is bypassed.
Prompts
- Where do we terminate TLS and then forward plaintext internally?
- Which services still accept TLS 1.0/1.1?
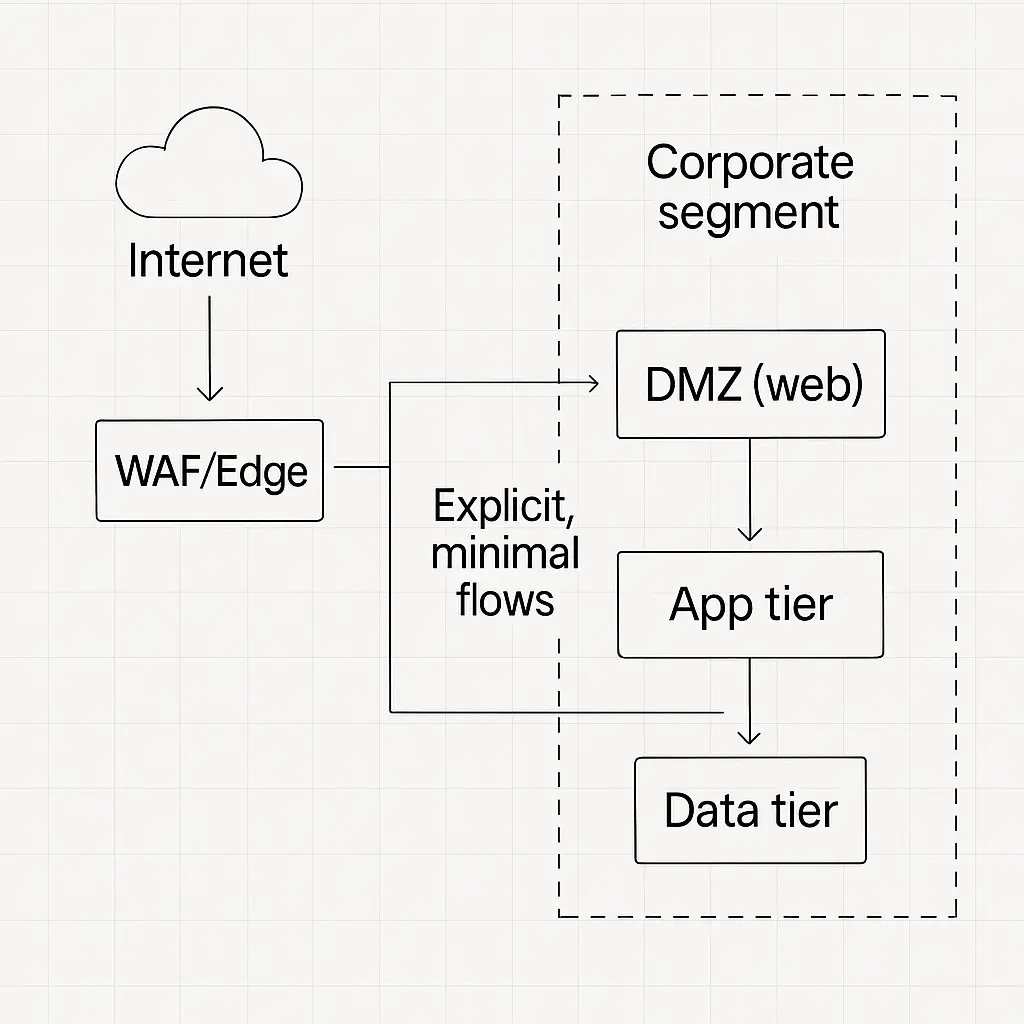
5. Network security: segment and observe
Assume breach and block lateral movement. CISA now frames microsegmentation as a foundational zero-trust step. PCI scoping guidance says segmentation also shrinks compliance scope and blast radius.
Developer checklist
- Put public web apps in a DMZ, app tier separate, and databases in a restricted zone. Only allow required flows.
- Require bastions or session proxies for admin access.
- Turn on detection: centralize logs, alert on odd data egress, and baseline service-to-service traffic. CIS Control 8 is your reference for logging.
Prompts
- If one kiosk or microservice is compromised, what stops it reaching your customer DB?
- Which east-west flows lack firewall or service-mesh policy?
6. Secure development by default
Bake security into the SDLC. Test for the things attackers still exploit most. OWASP Top 10 keeps Injection on the podium because parameterization and validation are still missed in codebases.
Developer checklist
- Threat-model in planning. Add "abuse cases" to user stories.
- Automate SAST/DAST/SCA in CI and block on severities you agree to in advance.
- Unit-test for authz boundaries. Add integration tests for IDOR and predictable resource locations.
- Use the OWASP MASVS/MASTG checklists for mobile.
Prompts
- Which endpoints accept user input that reaches a query or shell?
- Do we run a pre-release pen test for authz and business logic?
7. Manage third parties with evidence, not promises
Vendors extend your attack surface. Set explicit security requirements in contracts and verify them. This "trust but verify" stance aligns with the FTC's long-standing guidance to build oversight into service-provider relationships. Publish a clear path for researchers to report issues. The security.txt standard (RFC 9116) makes that easy.
Developer checklist
- Require encryption, access controls, logging, and secure disposal in contracts. Review SOC 2 or mapped controls.
- Collect and review provider logs for your tenant. CIS Control 8 covers service-provider logs.
- Host /.well-known/security.txt and route reports to a monitored inbox or ticket queue.
Prompts
- Which vendors process PII or card data for us today?
- Do we receive their audit logs and alerts in our SIEM?
8. Keep security current
Patching known issues prevents many incidents. Create a cadence and priority scheme. Also, make it easy for the outside world to tell you when something is wrong, then respond fast. Many breaches get worse because the organization never saw or routed the report correctly. The FTC's case summaries underline the need for a publicized vulnerability contact and a process behind it.
Developer checklist
- Automate dependency updates and container base-image refresh in CI. Track CVEs for internet-facing assets.
- Publish and maintain a vulnerability disclosure process and security.txt.
Prompts
- Where do we still patch by hand?
- Who owns triage for security@ mail?
9. Physical security still matters
Paper, laptops, POS terminals, and removable media get stolen. Treat physical exposure like any other risk: reduce what exists, lock what remains, and encrypt what must move. These basics are consistent with regulator post-incident guidance and with common control frameworks.
Developer checklist
- Encrypt all laptops and backups. Lock paper records and restrict access.
- Use tracked couriers for media. Prefer secure transfer over physical movement.
Prompts
- Which backups are unencrypted or travel offsite?
- Where do we print PII and why?
10. What to diagram
Two key diagrams help communicate and validate your security approach:
- Data lifecycle controls: collection → transit → storage → processing → third-party transfer → disposal, with controls noted at each hop.
- Network segmentation: Internet → WAF/Edge → DMZ (web) → App tier → Data tier, plus corporate segment, with explicit, minimal flows.
Appendix: "Secure by default" settings you can adopt this week
Quick Security Wins
Forms and events: delete three nonessential fields. Add a retention TTL to one PII table.
Auth: raise minimum length, enable breach-password screening, add rate-limits, and require MFA for password reset and payout actions.
Transport: enforce TLS 1.2+ everywhere, remove weak ciphers, and add CI checks for accidental cert-validation bypass in mobile.
Code scanning: add an injection-focused test step tied to OWASP A03 controls.
Logging: centralize and alert on auth anomalies and unusual egress. Base policy on CIS Control 8.
Vendor surface: publish /.well-known/security.txt, verify one critical provider's controls, and ingest their logs.
Notes on fact-checking and standards used
- Data minimization and "build it in" come from the FTC's Start with Security guide, a synthesis of lessons from enforcement actions.
- Password policy direction follows NIST SP 800-63B's move toward length, breach-screening, and throttling rather than composition myths.
- TLS requirements reference NIST SP 800-52r2 and current guidance to support TLS 1.3 and configure TLS 1.2 correctly.
- Mobile cert-validation risks are documented in OWASP MASTG and its demos.
- Injection remains common per OWASP Top 10 2021. Use parameterized queries and validation.
- Card data retention and the ban on storing SAD after authorization follow PCI DSS v4 Requirement 3 and retention guidance. Tokenize card data and minimize PAN storage.
- Logging and monitoring are anchored in CIS Control 8.
- Microsegmentation reflects recent CISA guidance on zero-trust.
- Vulnerability reporting: publish security.txt per RFC 9116.
Need Help Implementing These Security Practices?
Our security experts can help you assess your current posture and implement these essential practices without slowing down your development velocity.
Schedule a Security AssessmentNeed Expert Help With Your Project?
Our team of specialists is ready to help you implement the strategies discussed in this article and address your specific business challenges.